How computer viruses work
In a worm, the target locator might use a variety of techniques to find new machines to infect. It may, for example, raid your address book and send emails to everyone you know containing a copy of itself in an attachment, the Melissa did.
Some target locators generate a range of random IP addresses to try and infect. Others simply raid your computer's DNS cache and hosts file for addresses. Some use all of these techniques and more besides. Once the target locator finds another host running a suitable OS, it passes control to the infection propagator to find an infection vector.
Once a worm infects a new computer, it deploys its payload as well as propagating further. The payload might be something productive – collecting credit card details, perhaps – but many are simply destructive, as was 2004's Witty worm. Its payload deleted sections of the victim's hard disk.
Unlike virus writers, however, worm writers needn't simply fire and forget their work. In the mid-1990s, they began making their progeny call home to receive updates, new payloads and new infection vectors through control modules. And so, the 'botnet' worm was born.
Operated by criminal gangs and often consisting of upwards of a million infected machines, the great skill in creating a botnet is to build a command-and-control structure that's difficult to trace and resilient against attack while simultaneously open for the owner to issue orders, code updates and new payloads at will.
The average computer owner must therefore thwart several decades of continued, and often ingenious, malware development. Here's a technique that can give you 100 per cent protection, even after infection.
A digital Petri dish
Sign up for breaking news, reviews, opinion, top tech deals, and more.
We live in a world filled with very tempting free utilities served from obscure websites. However, we also live in a world where it's very easy to infect yourself by making hasty decisions. An abandoned website offering an executable for download offers the virus writer a stationary target.
Hacking the site of someone who has written a cool utility and then lost interest is an excellent way of starting a new worm infection. With the site cracked, the virus writer can infect the utility and re-upload it in place of the original.
If the virus uses a 'zero day' exploit, the infection will go unnoticed until a network security researcher finds it, a patch is released and antivirus companies issue an update.
In the meantime, you have no protection from the virus. Your machine may refuse to boot, your disk may become corrupt or you may be overrun with porn pop-ups. So, how can you protect yourself?
One method is to create a digital Petri dish – in this case a virtual machine that runs one operating system inside another – and run unknown programs in it to see how they behave. If a virus infects the virtual machine, it won't be able to infect the Linux host even if it escapes.
First of all you will need to download and install Sun Microsystem's VirtualBox software so you can run a virtual OS in order to safely test the virus file. However, setting up a virtual machine that will keep the rest of your network safe requires a small amount of configuration.
After you first install Windows into VirtualBox, take a snapshot. This allows you to turn back time at will without having to reinstall Windows. To take a snapshot, power down the virtual machine, select it in VirtualBox and select the Snapshot tab.
Press the button that looks like a camera. In the resultant dialogue box, enter a name and a description and click 'OK'. If you ever need to revert to this snapshot, right-click on it and select 'Revert to current snapshot'.
Before you run an unknown downloaded program, you must make sure that it can't spread any infectious malware to the rest of your network. With the virtual machine stopped, select its Details tab. Scroll down to the Network section and click it.
A dialogue box will open up that displays the details of the emulated network adaptor card. Untick the 'Enable network adaptor' checkbox to disable network activity. Now when you click to install a program, it can't escape the virtual machine.
If you do run into software that infects the virtual system, you can simply roll back to your previous snapshot and start again.
Test your antivirus
After installing or upgrading antivirus software, you need to be sure that it's working properly. However, it would be very foolish indeed to deliberately infect your machine. Luckily, though, there is a safe way to test that your software is identifying viruses correctly: infecting your system with a purpose-built fake virus.
The EICAR virus is a completely benign piece of test code that, if they're installed and working properly, all antivirus products should recognise and report as if it were a real infection, and offer to remove. EICAR stands for the European Institute for Computer Antivirus Research.
The virus that the Institute created is nothing more than a text file, but the viral signature that it carries should be in the databases of all antivirus products. The text that the file contains is as follows:
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUSTEST-FILE!$H+H*
You can paste this code directly into Notepad or you can copy and paste it from the official site. Either way, after you've entered the text, save the file as 'EICAR.COM'. The name ensures that the resident shield of your antivirus software will scan the file as an executable when you try to access it (you can open it again in Notepad for this).
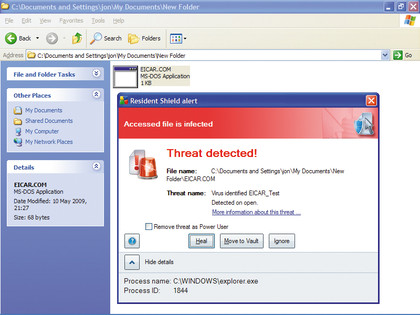
NOWHERE TO HIDE: If this file isn't detected by your antivirus it is time to get a new antivirus
A good antivirus system will be able to tell you the name of the virus. A really good one should be able to spot the file even when it's hidden in zipped archives. If your antivirus software doesn't detect EICAR, you have a problem.
First, reboot and try again. If there's still nothing, reinstall the antivirus package. If it still doesn't detect it, switch antivirus vendors immediately.